What Is a Cyberattack Chain?
A cyberattack chain refers to the sequence of events or steps that an attacker goes through to successfully compromise a target system or network. It typically consists of several stages, starting from initial reconnaissance and culminating in achieving the attacker's objective, such as stealing data or disrupting operations. Common stages in a cyberattack chain may include:
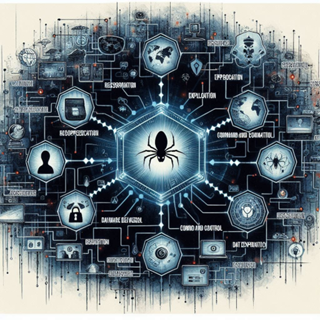
- Reconnaissance: Gathering information about the target, such as identifying vulnerabilities, system configurations, and potential entry points.
- Weaponization: Creating or obtaining the tools or malware necessary to exploit vulnerabilities discovered during reconnaissance.
- Delivery: Delivering the weaponized payload to the target system, often through methods like phishing emails, malicious websites, or compromised software.
- Exploitation: Using the weaponized payload to exploit vulnerabilities and gain unauthorized access to the target system or network.
- Installation: Installing additional tools or malware to establish persistence and maintain access to the compromised system.
- Command and Control (C2): Establishing communication channels between the attacker and the compromised system to remotely control it and exfiltrate data or carry out other malicious activities.
- Actions on Objectives: Achieving the attacker's goals, which could include stealing sensitive information, disrupting operations, or deploying ransomware.
Other similar frameworks or methods include MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge), which is a knowledge base of adversary tactics and techniques based on real-world observations. ATT&CK provides a more granular breakdown of specific tactics and techniques used by attackers, enabling organizations to better understand and defend against cyber threats.
The benefit of using a cyberattack chain or similar frameworks is that they provide a structured approach for understanding and analyzing cyber threats. By breaking down the attack process into distinct stages or techniques, security professionals can identify potential vulnerabilities, develop effective defense strategies, and prioritize security measures to mitigate the risk of successful cyberattacks. Additionally, these frameworks help organizations improve their incident response capabilities by providing a common language and reference point for discussing and addressing cybersecurity threats.


